More than ever, Industrie 4.0 and competitive pressures are pushing companies to find ways to access production data securely. What are the options? It turns out that some are better than others.
VPN exposure
VPNs are simply not adequate for secure access to plan data. A VPN effectively extends the security perimeter beyond the plant network to include the IT network, and IT networks are frequently hacked. A VPN between IT and OT exposes OT networks to the security risks facing IT.
OPC and MQTT not designed for DMZs
Another option is to combine OPC and MQTT for in-plant and plant-to-cloud security. This approach draws on the strengths of both protocols but falls short when it comes to NIS 2 recommendations to isolate networks using a DMZ. The OPC UA protocol is too complex to reproduce through a DMZ, and the QoS guarantees in MQTT cannot propagate well through a DMZ, making data at the user end unreliable.
Tunnel/mirror solution
A secure tunnel/mirror implementation can send data outbound from behind closed firewalls, as well as support connections across a DMZ. It mirrors the full data set at each node, and can provide access to that data, both for qualified clients as well as the next node in the chain. Such software can guarantee consistency across the DMZ connection, so that the data for any client or intermediate point in the chain will be consistent with the original source.
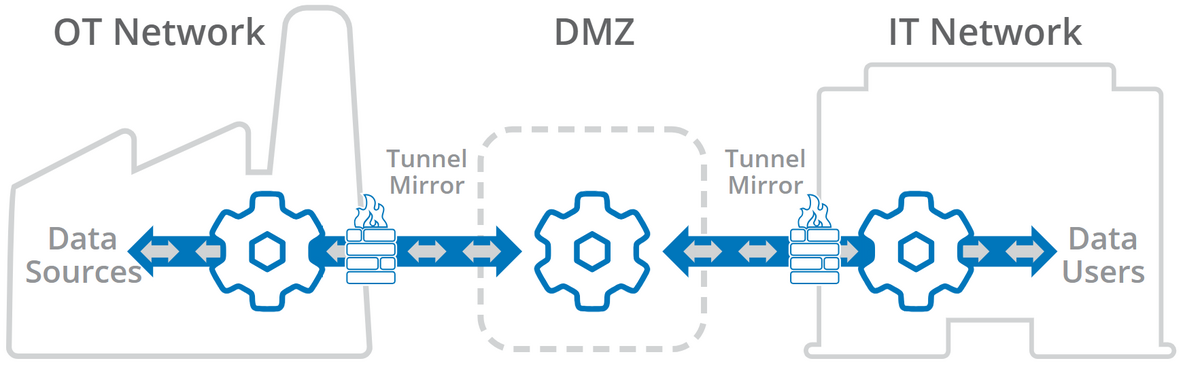
Image source:
https://cogentdatahub.com/media/datahub-tunnel-mirror-better-network-segmentation-2.svg
For secure access to your production data, keeping all inbound firewall ports closed and isolating networks with a DMZ, the best approach is tunnel/mirroring. DataHub Tunneller software from Skkynet offers a secure way to connect OT and IT systems for real-time data flow without compromising on cybersecurity, enabling companies to remain competitive without sacrificing security.







