There is, without doubt, value in process data. More and more companies are waking up to that reality. C-level executives and upper management are keen to extract that value using analytical tools and techniques provided by their IT departments.
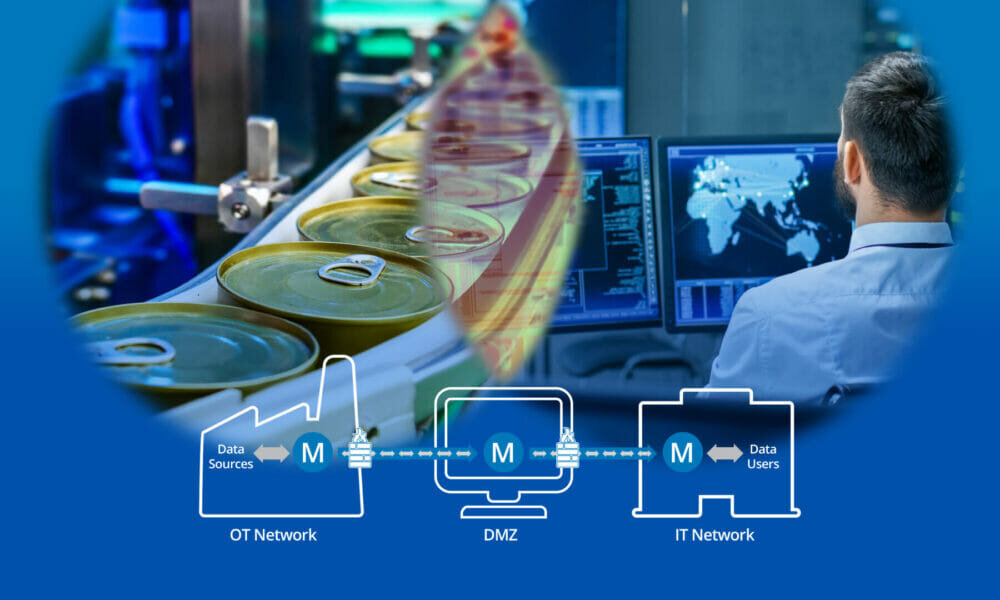
However, security is always an issue. Best practices dictate that OT and IT networks be completely isolated from each other. This can best be accomplished using a DMZ to ensure no direct link between corporate networks and control networks. Only known and authenticated actors can enter the system at all. Firewalls protect both the OT and IT sides, configured to allow only outbound connections to the DMZ. This ensures that only the correct data passes between networks.
To enable a secure, robust connection across a DMZ, and support real-time bidirectional communication, Skkynet recommends secure tunnelling. Well-designed tunnelling middleware can seamlessly aggregate a variety of industrial protocols like OPC, MQTT, and Modbus and send their data securely across a DMZ to clients running in IT or the cloud. There is no need for VPNs, and all inbound firewall ports can stay closed.
Anyone familiar with OPC UA or MQTT might ask, why not use one of those protocols to make the connection? Put simply, they weren’t designed for the task. Getting data out of a plant through a DMZ typically requires two or more servers, daisy chained together. The OPC UA protocol is simply too complex to reproduce well in a chain like this. MQTT requires each node in the chain to be individually configured, and the Quality of Service guarantees cannot propagate through the chain, making data unreliable.
Skkynet’s secure-by-design tunnelling solution connects and integrates OPC UA and MQTT protocols at either or both ends of the tunnel and supports bi-directional data transfer across a DMZ in real time.